
The intersection of artificial intelligence and systems security has reached a critical inflection point. As AI agents become increasingly capable of executing external tools and accessing system resources, the traditional security models that govern software execution are proving inadequate. Microsoft’s Wassette emerges as a groundbreaking solution that leverages WebAssembly’s sandboxing capabilities to create a secure, scalable runtime for AI tool execution through the Model Context Protocol (MCP).
Wassette represents a paradigm shift from the current landscape of MCP server deployment, where tools typically run with unrestricted system access, to a capability-based security model that provides fine-grained control over resource access. This architectural evolution addresses fundamental security concerns while maintaining the flexibility and extensibility that make MCP valuable for AI system integration. {{ responsive_image(src=“/images/blog/2025/09/2025-09-28-wassette-webassembly-mcp-microsoft-wasmtime-1181207.jpg”, alt=“Hands typing on a keyboard in a modern workstation”, caption=“Sandboxed execution with WebAssembly isolates tools from host system resources”, attribution=“Photo by Christina Morillo (Pexels)”, attribution_url=“https://www.pexels.com/photo/person-browsing-on-black-and-blue-laptop-computer-1181207/”) }}
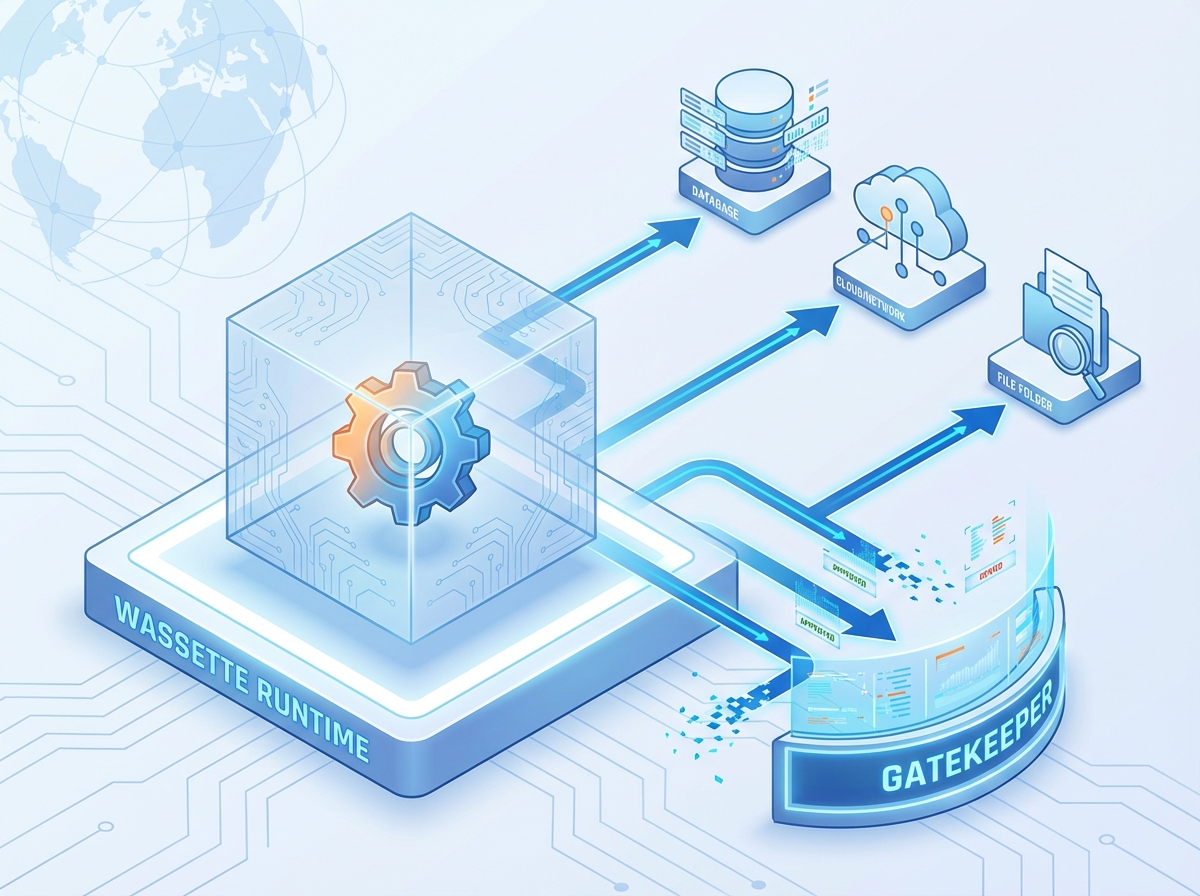
Understanding Wassette’s Architecture
Wassette (pronounced “Wass-ette,” a portmanteau of “Wasm” and “Cassette”) is an open-source MCP server implementation that runs WebAssembly Components in a secure sandbox environment. Unlike traditional MCP servers that execute as standalone processes with full system privileges, Wassette constrains tool execution within WebAssembly’s security boundaries while providing controlled access to system resources through explicit capability grants.
The architecture centers on three core principles:
Sandboxed Execution: Every tool runs within WebAssembly’s memory-safe, isolated execution environment, preventing unauthorized access to system resources, memory corruption vulnerabilities, and arbitrary code execution.
Capability-Based Security: Tools must explicitly request and receive permission for specific operations, including file system access, network connections, and environment variable access, following the principle of least privilege.
Component Model Integration: Wassette leverages the WebAssembly Component Model (WASM Components) to provide strongly-typed interfaces and interoperability between tools written in different programming languages.
The Security Imperative
Current MCP deployment patterns expose significant attack surfaces. Traditional approaches include:
- Direct Binary Execution: Tools run via package managers like
npxoruvxwith full system privileges - Container Isolation: While providing some boundaries, containers lack fine-grained permission controls
- Standalone Processes: MCP servers communicate via stdio or sockets but inherit host process privileges
These patterns create vulnerabilities where malicious or compromised tools can access arbitrary files, establish unauthorized network connections, or execute system commands. Wassette addresses these concerns by implementing a zero-trust security model where capabilities must be explicitly granted.
Technical Implementation and Architecture
Wassette’s implementation leverages Rust and the Wasmtime runtime to provide a high-performance, memory-safe foundation for WebAssembly execution. The architecture consists of several key components:
Core Runtime Components
Wasmtime Integration: Wassette builds on Wasmtime, Mozilla’s production-ready WebAssembly runtime, inheriting its security properties and performance optimizations. Wasmtime provides the foundational sandboxing that isolates WebAssembly modules from the host system.
MCP Protocol Bridge: The runtime translates between MCP’s JSON-RPC protocol and WebAssembly Component interfaces, enabling seamless integration with existing MCP clients while maintaining type safety through the Component Model’s interface definitions.
Permission Engine: A sophisticated policy engine manages capability grants and revocations, supporting both static policy definitions and dynamic permission management through MCP tools.

Component Model Integration
Wassette’s use of the WebAssembly Component Model represents a significant advancement over traditional WebAssembly modules. Components provide:
Strongly-Typed Interfaces: Tools expose their capabilities through WebAssembly Interface Types (WIT), enabling compile-time verification of interface compatibility and runtime type safety.
Language Agnostic Development: Components can be written in any language that compiles to WebAssembly, including Rust, JavaScript, Python, Go, and C++, while maintaining interface compatibility.
Composability: Components can be composed and linked together, enabling complex tool chains while maintaining isolation boundaries.
Here’s an example WIT definition for a simple time server component:
package local:time-server;
world time-server {
export get-current-time: func() -> string;
export get-timezone: func() -> string;
export format-time: func(timestamp: u64, format: string) -> string;
}This interface definition is completely generic—there’s nothing MCP-specific about it. Wassette automatically exposes these functions as MCP tools by introspecting the component’s interface.
Security Model and Permission System
Wassette implements a comprehensive permission system that provides granular control over resource access. The security model operates on three primary resource categories:
File System Access Control
Storage permissions control access to file system resources through URI-based patterns:
permissions:
storage:
allow:
- uri: "fs://workspace/**"
access: ["read", "write"]
- uri: "fs://config/app.yaml"
access: ["read"]
deny:
- uri: "fs://system/**"The permission system supports glob patterns for flexible path matching while maintaining security boundaries. Components can request read-only or read-write access to specific paths, and permissions can be granted or revoked dynamically.
Network Access Management
Network permissions control outbound connections to specific hosts and protocols:
permissions:
network:
allow:
- host: "api.openai.com"
protocols: ["https"]
- host: "*.github.com"
protocols: ["https"]
deny:
- host: "localhost"
- host: "127.0.0.1"This approach prevents tools from establishing unauthorized connections while enabling legitimate API access. The permission system can restrict access by hostname, IP address, port, and protocol.
Environment Variable Access
Environment variable permissions control access to system configuration:
permissions:
environment:
allow:
- key: "API_KEY"
- key: "USER_CONFIG_*"
deny:
- key: "SYSTEM_*"Components must explicitly request access to environment variables, preventing unauthorized access to sensitive configuration data.
Practical Implementation Examples
Building a Weather Component
Let’s examine a practical example of building a weather component for Wassette. This component demonstrates the integration of external API access with Wassette’s permission system.
First, define the component interface in WIT:
package weather:api;
world weather-server {
export get-weather: func(location: string) -> result<weather-data, error-info>;
export get-forecast: func(location: string, days: u32) -> result<forecast-data, error-info>;
}
record weather-data {
location: string,
temperature: f32,
humidity: f32,
description: string,
timestamp: u64,
}
record forecast-data {
location: string,
days: list<daily-forecast>,
}
record daily-forecast {
date: string,
high-temp: f32,
low-temp: f32,
description: string,
}
record error-info {
code: u32,
message: string,
}The implementation in Rust would look like:
use weather_api::*;
struct WeatherComponent;
impl Guest for WeatherComponent {
fn get_weather(location: String) -> Result<WeatherData, ErrorInfo> {
// Implementation requires network permission for weather API
let api_key = std::env::var("WEATHER_API_KEY")
.map_err(|_| ErrorInfo {
code: 401,
message: "API key not configured".to_string(),
})?;
// Make HTTP request to weather service
// This requires network permission for the weather API host
let response = make_weather_request(&location, &api_key)?;
Ok(WeatherData {
location,
temperature: response.temp,
humidity: response.humidity,
description: response.description,
timestamp: current_timestamp(),
})
}
}To use this component, you would need to grant appropriate permissions:
# Load the weather component
wassette load-component oci://ghcr.io/example/weather:latest
# Grant network permission for weather API
wassette grant-network-permission <component-id> api.openweathermap.org
# Grant environment variable access for API key
wassette grant-environment-variable-permission <component-id> WEATHER_API_KEYFile System Operations Component
Here’s an example of a component that performs file system operations with appropriate permission controls:
package filesystem:ops;
world filesystem-server {
export read-file: func(path: string) -> result<string, error-info>;
export write-file: func(path: string, content: string) -> result<unit, error-info>;
export list-directory: func(path: string) -> result<list<string>, error-info>;
}The component would require explicit storage permissions:
# Grant read access to workspace directory
wassette grant-storage-permission <component-id> fs://workspace/** read
# Grant write access to output directory
wassette grant-storage-permission <component-id> fs://output/** write
Performance Characteristics and Optimization
Wassette’s performance profile reflects the efficiency of modern WebAssembly runtimes combined with Rust’s zero-cost abstractions. Key performance characteristics include:
Memory Efficiency
WebAssembly’s linear memory model provides predictable memory usage patterns. Components operate within isolated memory spaces, preventing memory leaks from affecting other components or the host system. Memory overhead is significantly lower than container-based isolation, with typical components requiring only a few megabytes of memory.
Execution Performance
Wasmtime’s ahead-of-time compilation and optimization pipeline delivers near-native performance for WebAssembly code. Benchmarks show that well-optimized WebAssembly components can achieve 80-95% of native performance for compute-intensive operations.
Startup Latency
Component instantiation is optimized for low latency, with typical startup times under 10 milliseconds for simple components. This enables responsive tool execution without the overhead associated with container startup or process spawning.
Scalability Characteristics
Wassette’s architecture supports horizontal scaling through component isolation. Multiple instances of the same component can run concurrently without interference, and the permission system ensures that resource access remains controlled across all instances.
Integration with MCP Clients
Wassette integrates seamlessly with existing MCP clients through its standards-compliant MCP server implementation. The integration process varies by client but follows consistent patterns:
Visual Studio Code Integration
For VS Code with GitHub Copilot:
# Install Wassette MCP server
code --add-mcp '{"name":"Wassette","command":"wassette","args":["serve","--stdio"]}'Claude Desktop Integration
Add to Claude’s MCP configuration:
{
"mcpServers": {
"wassette": {
"command": "wassette",
"args": ["serve", "--stdio"]
}
}
}Cursor Integration
Configure in Cursor’s settings:
{
"mcp.servers": {
"wassette": {
"command": "wassette serve --stdio"
}
}
}Component Distribution and Registry
Wassette leverages OCI (Open Container Initiative) registries for component distribution, providing a familiar and robust distribution mechanism. Components are packaged as OCI artifacts with cryptographic signatures for integrity verification.
Publishing Components
Components can be published to any OCI-compatible registry:
# Build and publish a component
wasm-tools component new target/wasm32-wasi/release/weather.wasm -o weather.wasm
oras push ghcr.io/username/weather:latest weather.wasmComponent Discovery
Wassette includes a component registry that catalogs available components:
# Search for available components
wassette search-components
# Load a component from the registry
wassette load-component oci://ghcr.io/microsoft/time-server-js:latestDevelopment Workflow and Tooling
The development workflow for Wassette components emphasizes simplicity and developer productivity:
Language Support
Wassette supports components written in any language that can compile to WebAssembly Components:
- Rust: First-class support with
cargo component - JavaScript/TypeScript: Via
jco(JavaScript Component Tools) - Python: Via
componentize-py - Go: Via TinyGo with component model support
- C/C++: Via Clang with WASI support
Development Tools
Essential tools for component development:
# Install component development tools
cargo install cargo-component
npm install -g @bytecodealliance/jco
pip install componentize-py
# Create a new Rust component
cargo component new my-tool
cd my-tool
cargo component buildTesting and Debugging
Wassette provides comprehensive testing and debugging capabilities:
# Test component locally
wassette test-component ./target/wasm32-wasi/release/my-tool.wasm
# Debug component execution
wassette debug-component <component-id> --verboseCurrent Development Status and Roadmap
Wassette is actively developed by Microsoft with regular releases and community contributions. The project has achieved significant milestones:
Current Status (v0.2.0)
- Production Ready: Stable MCP server implementation with comprehensive permission system
- Multi-Language Support: Components can be written in Rust, JavaScript, Python, and Go
- OCI Integration: Full support for component distribution via OCI registries
- Client Compatibility: Works with all major MCP clients including VS Code, Claude, and Cursor
Roadmap and Future Development
Enhanced Security Features: Advanced sandboxing capabilities, formal verification of permission policies, and integration with hardware security modules.
Performance Optimizations: Improved component caching, lazy loading optimizations, and enhanced memory management.
Developer Experience: Integrated development environment support, enhanced debugging tools, and automated component testing frameworks.
Ecosystem Expansion: Broader language support, component composition tools, and marketplace integration for component discovery.
Comparative Analysis with Alternative Solutions
Wassette’s approach differs significantly from other MCP deployment strategies:
Container-Based Isolation
Traditional container approaches provide process-level isolation but lack fine-grained permission controls. Containers also incur higher memory overhead and slower startup times compared to WebAssembly components.
Direct Binary Execution
Running MCP servers as native binaries offers maximum performance but provides no security boundaries. This approach is suitable for trusted environments but inappropriate for executing third-party tools.
Centralized WebAssembly Platforms
Some platforms run WebAssembly tools centrally but require custom ABIs and lack interoperability. Wassette’s use of the Component Model ensures compatibility across different runtimes and tools.
Conclusion
Wassette represents a significant advancement in AI tool security and deployment architecture. By combining WebAssembly’s sandboxing capabilities with the Model Context Protocol’s standardized interface, Wassette enables secure execution of untrusted tools while maintaining the flexibility and extensibility that make AI agents powerful.
The project’s emphasis on capability-based security, component interoperability, and developer experience positions it as a foundational technology for the next generation of AI systems. As AI agents become more prevalent and capable, the security guarantees provided by Wassette will become increasingly critical for enterprise adoption and user trust.
For developers building AI tools, Wassette offers a compelling alternative to traditional deployment models, providing security without sacrificing functionality. The Component Model’s language-agnostic approach ensures that existing tools can be adapted to run in Wassette’s secure environment, while new tools can be built with security as a foundational principle.
The future of AI tool execution lies in architectures that balance capability with security, and Wassette demonstrates how WebAssembly and thoughtful system design can achieve this balance effectively.
Was this helpful?
Have questions about this article?
Ask can help explain concepts, provide context, or point you to related content.